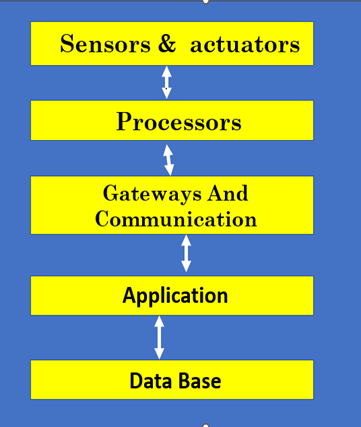
Host-level security in the cloud
Definition
· Cloud protects individual hosts as virtual machines (vms), containers, or physical servers in a cloud environment from threats, unauthorized access, and vulnerabilities.
· Features of Host-Level Security
Host-level security encompasses
several key features in cloud environments:
1. Operating System Protection:
2. Application Security:
3. Access Control:
4. Data Protection:
5. Threat Detection and Response:
6. Isolation:
Types of
Host-Level Security
Host-level security can be
categorized based on the focus area or approach:
1. Operating System Security:
2. Application Security:
3. Endpoint Security:
4. Container Security:
5. Host-Based Intrusion Detection/Prevention:
Tools for Host-Level Security
Several tools are commonly used to
implement host-level security in cloud environments.
1. Operating System Hardening:
- Center for Internet Security Benchmarks (CIS Benchmarks):
- Ansible/Puppet/Chef:
2. Endpoint Security:
- CrowdStrike Falcon:
- Carbon Black:
3. Container Security:
- Aqua Security:
- Twistlock (Prisma Cloud):
4. Host-Based Intrusion Detection:
- OSSEC:
- Tripwire:
5. Antivirus/Anti-Malware:
- Sophos:
- McAfee:
6. Cloud-Native Tools:
- AWS Systems Manager:
- Azure Security Centre:
- Google Cloud Security Command Centre:
Techniques for Host-Level Security
To secure a host, several
techniques are employed:
1. OS Hardening:
2. Patch Management:
3. Access Control:
4. File Integrity Monitoring:
5. Logging and Monitoring:
6. Network Segmentation:
7. Encryption:
Advantages of Host-Level Security
1. Granular Control:
2. Défense-in-Depth:
3. Threat Containment:
4. Compliance Support:
5. Flexibility:
Limitations of
Host-Level Security
1. Resource Intensive:
2. Scalability Challenges:
3. Misconfiguration Risks:
4. Dependency on Cloud Provider:
5. Limited Scope:
6. Insider Threats:
=============================================================

0 Comments