Generations of Computers
Generations of Computers The generation of computers refers to the classification of computers based on the core hardware technology , programming languages , and capabilities used during a particular period. Computers are broadly divided into five generations . 1️. First Generation Computers (1940–1956) Technology: Vacuum Tubes Description First-gen…
Read moreFeatures, additional features of C++11, C++14, and C++17,
Features, additional features of C++11, C++14, and C++17, Evolution of Modern C++ Before C++11 , C++ was powerful, but: Very verbose Manual memory management Poor multithreading support Difficult generic programming -------------------------------------------------------------------------------------- C++11 (Maj…
Read moreTemplates in C++
Templates A template in C++ is a mechanism that allows us to write generic programs , meaning the same code works for different data types . Needs of Templates Without templates: We must write separate functions/classes for int, float, double, etc. Code duplication increases Maintenance becomes difficult With Templ…
Read moreSearch This Blog
- January 20261
- December 202550
- November 202514
- August 20255
- July 20257
- June 20252
- May 20253
- April 20252
- January 20251
- September 202433
- August 20243
- May 20241
- April 202411
- March 202413
- February 20249
- January 202447
- December 20233
- November 20233
- October 20235
- April 20231
- December 20223
- November 20221
- June 202224
- May 202223
- April 20226
- March 20226
- February 202230
- January 20229
- December 20214
- October 20215
- August 20212
- June 20215
- May 202113
- April 20219
- March 20219
- January 20211
- December 202023
- September 20201
- August 202015
- July 20204
- June 20207



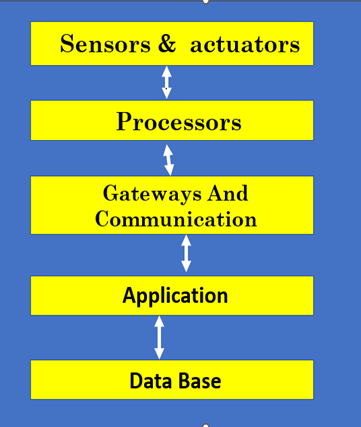
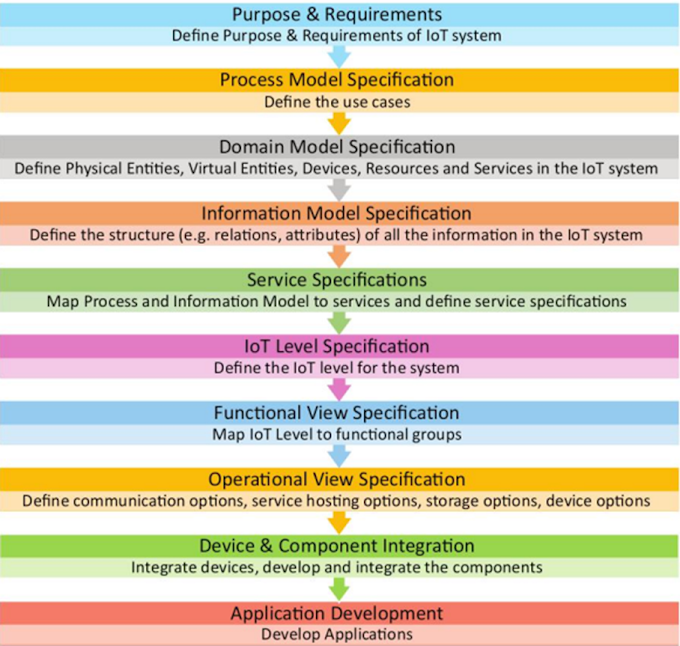
Social Plugin