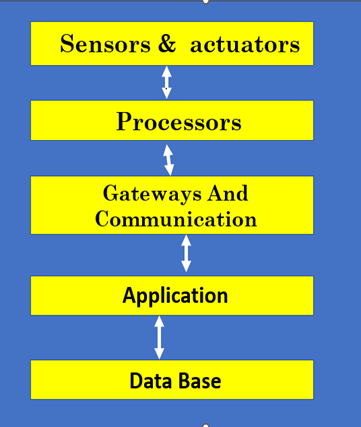
INFRASTRUCTURE SECURITY
Definition
Security of the IT environment,
including hardware, networks, virtual machines, storage, and operating systems,
whether on-premises or in the cloud, against threats such as unauthorized access, data
breaches, or service disruptions.
Features of Infrastructure Security
1. Comprehensive Protection:
2. Scalability:
3. Automation:
4. Shared Responsibility:
5. Compliance Integration:
6. Resilience(flexibility):
Types of Infrastructure Security
Categorized based on the components
it protects:
1. Physical Infrastructure Security:
- Protects data centres, servers, and hardware.
2. Network Security:
- Secures data transmission and network connectivity.
3. Compute Security:
- Protects virtual machines (VMs), containers, and serverless functions.
4. Storage Security:
- Safeguards data stored in cloud databases, object storage (e.g., AWS
S3), or block storage.
5. Endpoint Security:
- Secures devices (laptops, mobiles) accessing cloud infrastructure.
Tools for Infrastructure Security
1. Cloud-Native
Tools:
- AWS:
GuardDuty, Inspector, CloudTrail.
- Microsoft Azure: Azure Defender, Azure
Security Center.
- Google Cloud:
Security Command Center, Chronicle.
2. Third-Party
Tools:
- Palo Alto Prisma Cloud:
- CrowdStrike Falcon:
- Splunk:
- Tenable Nessus:
3. Open-Source
Tools:
- Wazuh:
- Falco:
Techniques for Infrastructure Security
1. Encryption:
2. Identity and Access Management (IAM):
3. Network Segmentation:
4. Patch Management:
- Regularly update.
5. Threat Detection and Response:
- Deploy Intrusion Detection/Prevention Systems (IDS/IPS) and SIEM
solutions.
- Example: Use AWS GuardDuty to detect malicious activity in real time.
6. Configuration Management:
7. Zero Trust Architecture:
8. Backup and Disaster Recovery:
Advantages of Infrastructure Security
1. Enhanced Protection: .
2. Compliance: .
3. Scalability:
4. Automation:
5. Resilience:
6. Cost Efficiency:
Limitations of Infrastructure Security
1. Complexity:
2. Misconfiguration Risks:
3. Cost:
4. Shared Responsibility Confusion:
5. Evolving Threats:
6. Skill Gaps:
================================================================

0 Comments