Characteristics of the Database Approach
· A systematic, structured, and integrated methodsà for managing, storing, and retrieving large volumes of information using a Database Management System (DBMS).· Remove drawbacks of traditional file-based data storage.
· Providing a centralized, efficient, and organized way to handle information.
Key Features of the Database Approach:
- Data Abstraction:
- Data Integrity and Consistency:
- Reduced Data Redundancy:
- Data Security:
- Concurrent Access and Multi-User Support:
- Backup and Recovery:
- Centralized Storage:
- Data Independence:
- Query Capability:
- Security and Integrity:
Example:- ERP, CRM, and business intelligence systems.
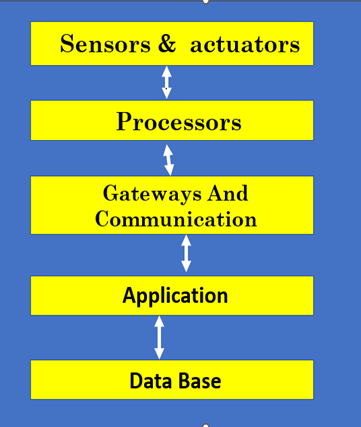
Core Components of the Database Approach:
DatabaseDatabase Schema
Data Models
Query Language (SQL)
Advantages of the Database Approach:
Data Consistency and Integrity: Ensures accuracy and reliability.Reduced Redundancy: Avoids duplicate data storage.
Efficient Data Management: Supports complex queries and transactions.
Scalability: Easily accommodates growth in data volume.
Data Security: Controls access and permissions.
Multi-User Support: Enables concurrent access by multiple users.
Applications of the Database Approach:
Business Applications:Healthcare:
Banking and Finance:
Education:
E-commerce:
Disadvantages
- Increase complexity and cost (e.g., DBMS software, hardware).- Centralized control.
- Required skilled personnel for administration.
===================================================

0 Comments